Today, FoxIT published an blog post with an github repository listing potential CobaltStrike servers for the last few years.
I was interested in the data so I processed the data with my osint-timesketch scripts to add passiveDNS and passiveSSL data. I only took the IPs that where last seen >2019 to not create to much data.
Adding it to timesketch was pretty straight forward:
sudo tsctl csv2ts -f output_cobalt.csv --name cobalt_strike
Indexing progress: 23000 events
Total events: 23650
Some quick findings, after searching for google I discovered several weird certificates, among them.

Some weird things: safebrowsing(.)net is not owned by google, the IP to that certificate accoring to Virustotal https://www.virustotal.com/#/ip-address/204.154.199.184 is resolving to microsoftapis(.)com – for sure nothing good.
Some other funny things where found by a quick look…
Hack me if you can
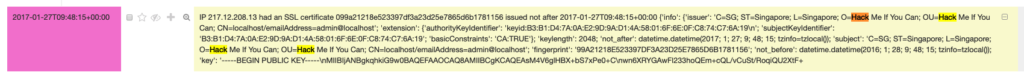
Happy Hacker fake CA
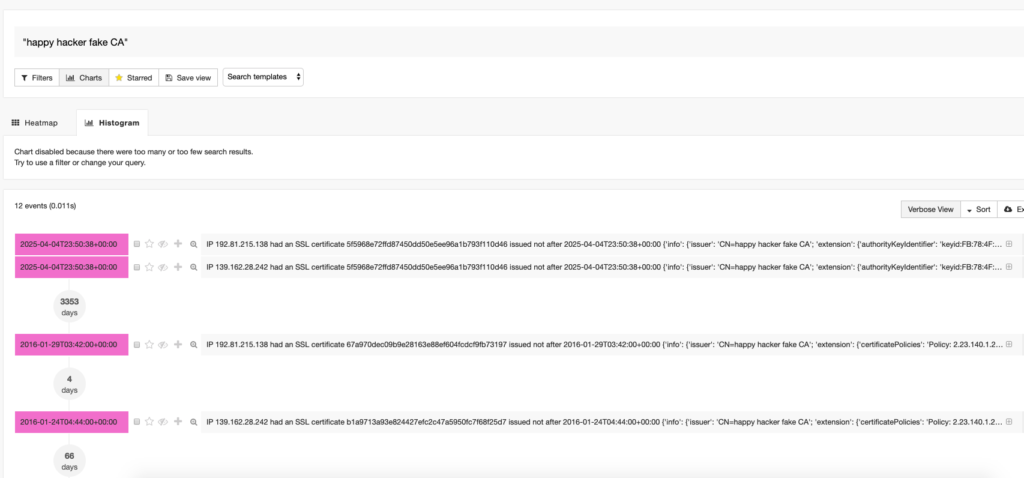
This outlines the importance of:
- Share the data (kudos FoxIT!)
- Provide researchers access to data sets (thx to CIRCL and Virustotal!)
My dataset is available on github.
