Motivation
Playing with Timesketch for a while and working on some OSINT timelines I was tired to investigate MD5 and domains / ips all manually so I tried to automate some of the work. Why is that important? If you have a list of hashes, domains and IPs, you of course can check your SIEM, EDR solution etc – but what if you have a hit? Would it benefit your investigation to at least have an idea of the timeframe something was used by attackers or seen in the wild?
Most shared indicators are lacking the timeframe, so we need to add those values by external information on our own.
Virustotal
There is no need to further explain Virustotal, it is basically a huge dataset of malware and information about domains and ips.
In particular information about a specific point in time a domain was seen to point to an IP and back is good to know to build your timeline.
E.g. if you have verymalicious.com pointing to 127.0.0.1 all the time, only on one day it was pointing to 1.2.3.4 – hits in your infrastructure should be higher escalated if seen during that day, out of that time window it might still be important, but not as urgent as during that day.
In regards to hash intelligence, Virustotal is nice, because if you add the info, when the last scan date of a file was, you can at least tell, that the file was known after that day.
I asked Virustotal to add more information they already have to the API and we will have wait till it is exposed:
- First seen in the wild
- First uploaded to VT
- PE compile time
PassiveSSL
Alexandre Dulaunoy and Eireann Leverett have given a talk at the FIRST conference in Berlin back in 2015, which took my attention, but it took some time till I really had time to implement something to use the idea.
The basic idea is that, out of several sources, passive ssl services such as CIRCL passiveSSL collect certificates and expose information via API.
For timeline analysis in particular, the following dates are important as they might shine some light of attacker activity:
- first seen in the wild
- last seen in the wild
- not use before
- not use after
If you now add all of the information above, you might be able to get a better idea, when an IP / Domain / File was active.
This information should then be fed into a Timesketch investigation.
Example
Using some sample data from APT33: https://github.com/deralexxx/osint-timelines/blob/master/2018/2018-12-21.OVERRULED:-Containing-a-Potentially-Destructive-Adversary-APT33.csv
Combining with the python script below with the following indicators:
basepack.org
103.236.149.124
5.79.66.241
8d3fe1973183e1d3b0dbec31be8ee9dd
fa7790abe9ee40556fb3c5524388de0b
Findings
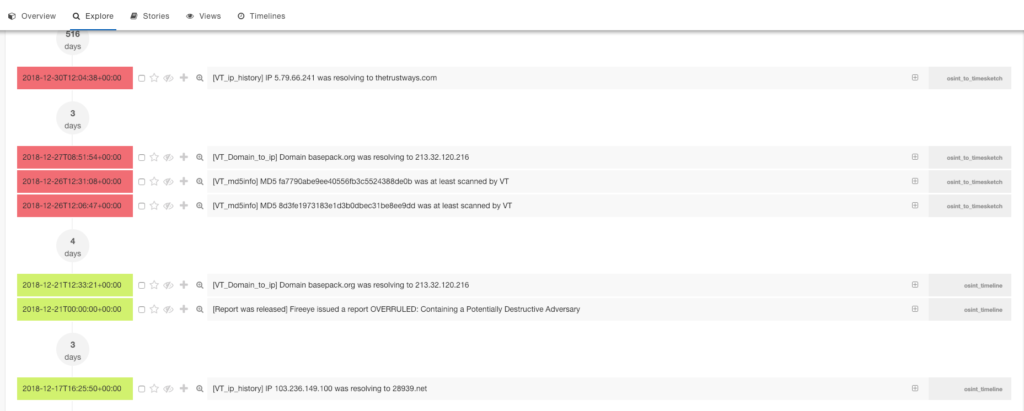
It is transparent when the hashes have been last scanned and what Ips resolve to the domains mentioned in the report.
The other thing is that right before some malware was mentioned by Fireeye in the report, SSL certificates became invalid:
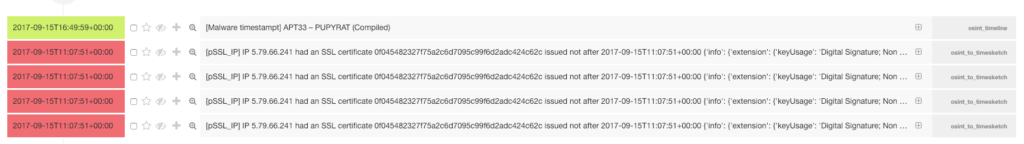
SSL Certificate
Of course the individual SSL certificate can also been investigated:
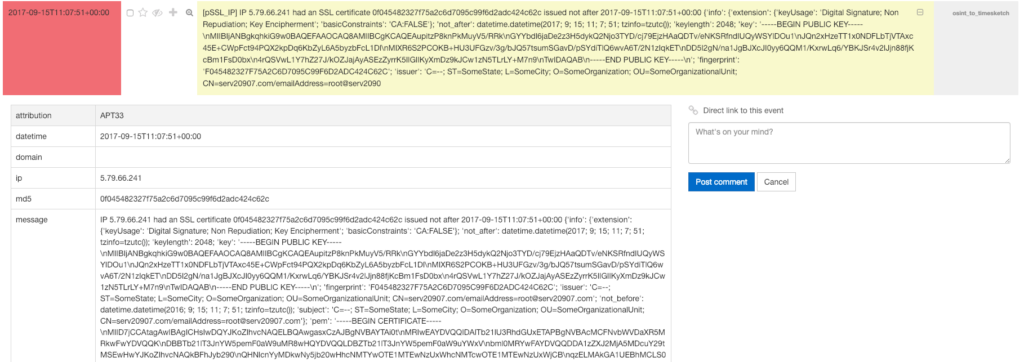
Python
The example is available on github: https://github.com/deralexxx/osint_to_timesketch
Next steps
- Waiting for VT to expose more things
- Improve the script
- Introduce multiple pDNS providers
